Penetration Testing
Penetration testing, also known as pen testing, is a cybersecurity technique used to identify and exploit vulnerabilities in computer systems, networks, or applications. The primary goal of a penetration test is to simulate a real-world attack by attempting to gain unauthorized access to the target system or network. This can involve a variety of techniques, such as attempting to exploit software vulnerabilities, guessing passwords, or using social engineering tactics to trick users into providing sensitive information.
A typical penetration test involves a combination of automated and manual techniques, including vulnerability scanning, network mapping, and reconnaissance, followed by attempts to exploit identified vulnerabilities. Penetration testers often use specialized tools and techniques to simulate various types of attacks, such as SQL injection, cross-site scripting, or buffer overflows. The results of a penetration test are usually presented in a detailed report that identifies vulnerabilities and provides recommendations for remediation. Penetration testing is an important component of a comprehensive security program and can help organizations identify weaknesses before they can be exploited by malicious actors.
Penetration Tetsing vs Vulnerbaility Assessments
Vulnerability assessment and penetration testing are both important techniques used in the field of cybersecurity, but they have different objectives and approaches. Here are some key differences between the two:
Objective: The main objective of a vulnerability assessment is to identify vulnerabilities in a system or network, while the main objective of a penetration test is to identify vulnerabilities and exploit them to gain unauthorized access or control over the system or network.
Scope: A vulnerability assessment typically focuses on identifying and categorizing vulnerabilities across an entire system or network, while a penetration test is usually more targeted and specific, focusing on a specific application, system, or network segment.
Methodology: Vulnerability assessments are typically conducted using automated tools and techniques that scan systems and networks for known vulnerabilities, such as missing security patches, weak passwords, or misconfigured settings. Penetration testing, on the other hand, often involves a combination of automated and manual techniques, including social engineering, to identify vulnerabilities and attempt to exploit them.
Reporting: A vulnerability assessment report typically provides a detailed list of vulnerabilities and recommendations for remediation. A penetration testing report, in addition to identifying vulnerabilities, also includes information about how successful attackers were in exploiting them, including the potential impact on the system or network.
Authorization: Vulnerability assessments can be conducted with or without the explicit authorization of the system owner or administrator, while penetration testing requires explicit authorization from the owner or administrator and is typically conducted with their oversight and cooperation.
In summary, vulnerability assessments and penetration testing are both important tools for identifying and addressing security weaknesses, but they differ in their objectives, scope, methodology, reporting, and authorization requirements.
Penetration testing can also be useful for determining:
How well the system tolerates real world-style attack patterns
The likely level of sophistication an attacker needs to successfully compromise the system
Additional countermeasures that could mitigate threats against the system
Defenders’ ability to detect attacks and respond appropriately.
Cyber D utilizes the NIST methodology which is a widely adopted approach to performing penetration testing that is effective in testing the security of the CLIENT’s network. All of the examinations are conducted with publicly available and commercial tools.
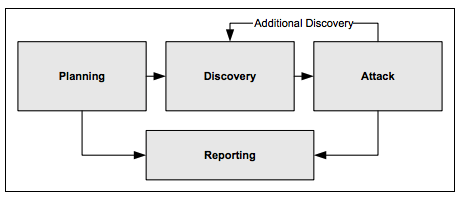
External Penetration Tests follow best practice in penetration testing methodologies which generally includes 4 phases:
Planning Phase:
In the planning phase, rules are identified, the scope is determined, management approval is finalized and documented, and testing goals are set. The planning phase sets the groundwork for a successful penetration test. No actual testing occurs in this phase.
Discovery Phase:
The discovery phase of penetration testing includes two parts. The first part is the start of actual testing, and covers information gathering and scanning. Network port and service identification is conducted to identify potential targets. In addition to port and service identification, other techniques are used to gather information on the targeted network
Host name and IP address information can be gathered through many methods, including DNS interrogation, InterNIC (WHOIS) queries, and network sniffing (generally only during internal tests)
Employee names and contact information can be obtained by searching the organization’s Web servers or directory servers
System information, such as names and shares can be found through methods such as NetBIOS enumeration (generally only during internal tests) and Network Information System (NIS) (generally only during internal tests)
Application and service information, such as version numbers, can be recorded through banner grabbing.
The second part of the discovery phase is vulnerability analysis, which involves comparing the services, applications, and operating systems of scanned hosts against vulnerability databases (a process that is automatic for vulnerability scanners) and the testers’ own knowledge of vulnerabilities.
Attack Phase:
Executing an attack is at the heart of any penetration test and represents the individual steps of the attack phase—the process of verifying previously identified potential vulnerabilities by attempting to exploit them. While vulnerability scanners check only for the possible existence of a vulnerability, the attack phase of a penetration test exploits the vulnerability to confirm its existence. If an attack is successful, the vulnerability is verified and safeguards are identified to mitigate the associated security exposure.
In many cases, exploits that are executed do not grant the maximum level of potential access to an attacker. They may instead result in the testers learning more about the targeted network and its potential vulnerabilities, or induce a change in the state of the targeted network’s security. Some exploits enable testers to escalate their privileges on the system or network to gain access to additional resources.
Reporting Phase:
The reporting phase occurs simultaneously with the other three phases of the penetration test. In the planning phase, the assessment plan, commonly called the “Rules of Engagement” is developed. In the discovery and attack phases, written logs are usually kept and periodic reports are made to system administrators and/or management. At the conclusion of the test, Cyber D prepares a report that describes identified vulnerabilities, present a risk rating, and give guidance on how to remediate the discovered weaknesses.